How to disable weak versions of SSL/TLS Protocols on Windows Servers
Hi, in this post, I want to show you how to disable the weak versions of the Transport Layer Security (TLS) and Secure Socket Layer (SSL) protocols using Windows PowerShell. Surely, before disabling weak versions of SSL / TSL protocols, you will want to make sure that you can use the TLS 1.2 protocol on your system.
In the following table, you can see the protocols that are compatible with the Windows operating system.
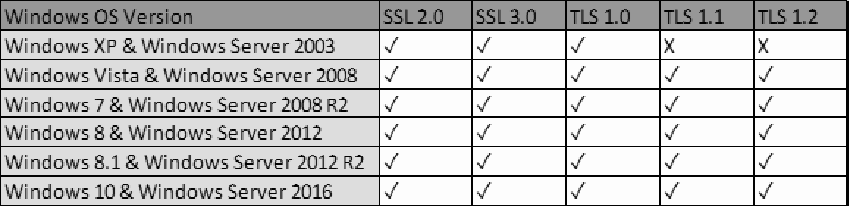
- Windows Server 2008 SP2: KB3154517
- Windows Server 2008 R2: KB3154518
- Windows Server 2012: KB3154519
- Windows Server 2012 R2: KB3154520
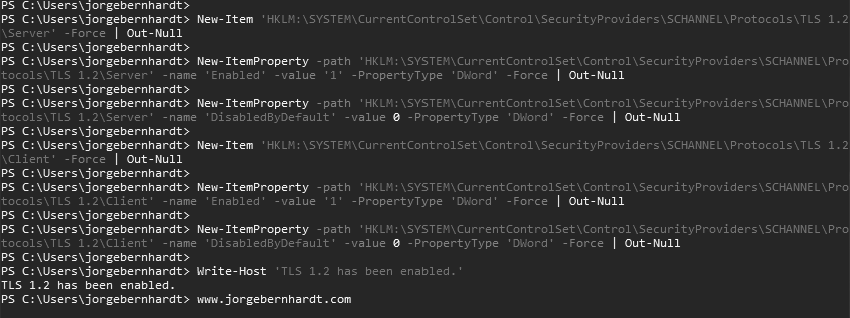
Enable TLS 1.2 #
To enable the TLS v1.2, open a Windows PowerShell command prompt as administrator and run the following commands:
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' `
-name 'Enabled' `
-value '1' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' `
-name 'DisabledByDefault' `
-value 0 `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' `
-name 'Enabled' `
-value '1' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' `
-name 'DisabledByDefault' `
-value 0 `
-PropertyType 'DWord' `
-Force `
| Out-Null
Write-Host 'TLS 1.2 has been enabled.'
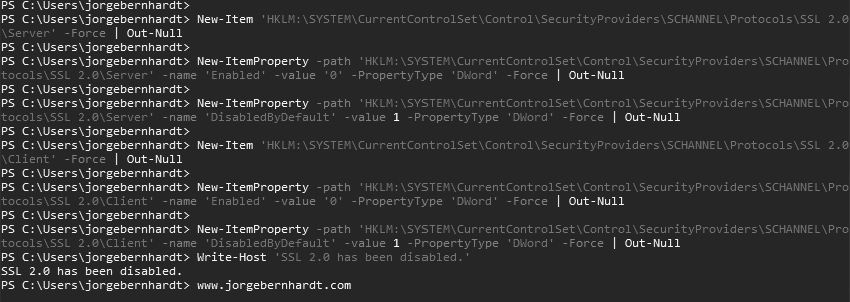
Disabling SSL 2.0 and SSL 3.0 #
To disable the SSL v2.0, open a Windows PowerShell command prompt as administrator and run the following commands:
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' `
-name 'Enabled' `
-value '0' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' `
-name 'DisabledByDefault' `
-value 1 `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' `
-name 'Enabled' `
-value '0' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' `
-name 'DisabledByDefault' `
-value 1 `
-PropertyType 'DWord' `
-Force `
| Out-Null
Write-Host 'SSL 2.0 has been disabled.'
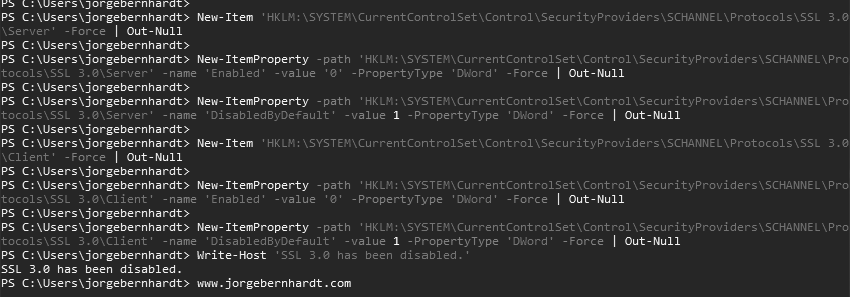
In the PowerShell console, run the following commands as an administrator to disable SSL v3.0:
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' `
-name 'Enabled' `
-value '0' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' `
-name 'DisabledByDefault' `
-value 1 `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' `
-name 'Enabled' `
-value '0' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' `
-name 'DisabledByDefault' `
-value 1 `
-PropertyType 'DWord' `
-Force `
| Out-Null
Write-Host 'SSL 3.0 has been disabled.'

#

Disabling TLS 1.0 and 1.1 #
To disable the TLS v1.0, open a Windows PowerShell command prompt as administrator and run the following commands:
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' `
-name 'Enabled' `
-value '0' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' `
-name 'DisabledByDefault' `
-value 1 `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' `
-name 'Enabled' `
-value '0' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' `
-name 'DisabledByDefault' `
-value 1 `
-PropertyType 'DWord' `
-Force `
| Out-Null
Write-Host 'TLS 1.0 has been disabled.'
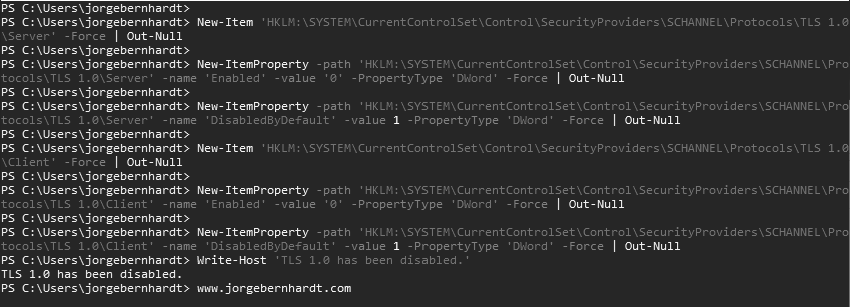
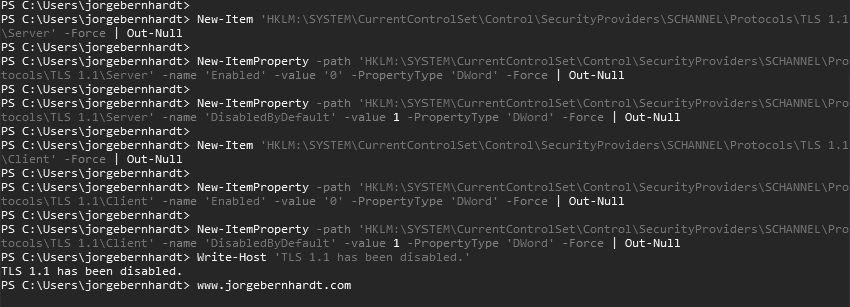
and run the following commands to disable version 1.1 of TLS:
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' `
-name 'Enabled' `
-value '0' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' `
-name 'DisabledByDefault' `
-value 1 `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-Item `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' `
-name 'Enabled' `
-value '0' `
-PropertyType 'DWord' `
-Force `
| Out-Null
New-ItemProperty `
-path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' `
-name 'DisabledByDefault' `
-value 1 `
-PropertyType 'DWord' `
-Force `
| Out-Null
Write-Host 'TLS 1.1 has been disabled.'
If you want to know why you should disable the weak versions of SSL/TSL protocols, check out this link.
