How to configure Azure Key Vault diagnostic settings
One of the security recommendations established by Microsoft in Azure Security Center is to enable diagnostic logs in Key Vaults. This lets you know how, when, and by whom your key vaults are accessed. In this post, I want to show you how to configure Azure Key Vault diagnostic settings to send logs and metrics to a storage account using PowerShell and Azure CLI.
Prerequisites #
- This tutorial assumes that you already have an Azure Storage account. You can use an existing Storage Account, or if you want to create a new one, check out this link.
- This tutorial assumes that you already have an Azure Key Vault. You can use an existing Key vault, or if you want to create a new one, check out this link.
Important: The storage account must be in the same subscription as your Azure Key Vault. #
In the following examples, I will separately enable event and metric logging for Key Vault. This action can be done with a single command, but I prefer to run them separately to show you in more detail. Also, I will set the retention policy to 365 days, but if you do not want to apply any retention policy and retain data forever, set retention (days) to 0.
Azure PowerShell Workaround #
The simplest way to get started is to sign in interactively at the command line.
Connect-AzAccount
This cmdlet will bring up a dialog box prompting you for your email address and password associated with your Azure account. If you have more than one subscription associated with your mail account, you can choose the default subscription. To perform this task, we will use the following commands:
Get-AzSubscription
Select-AzSubscription -Subscription "My Subscription"
Once you set your default subscription, you’re ready to start.
Set the variables #
Here, we define the characteristics of our environment and the resource’s properties.
$resourceGroupName="RG-DEMO-WE"
$keyVaultName="KV-DEMO-WE"
$storageAccountName="stoaccdemowe"
To improve the visualization of the following commands, I will store the resources into variables.
$keyvault= Get-AzKeyVault `
-Name $keyVaultName `
-ResourceGroupName $ResourceGroupName
$storageaccount = Get-AzStorageAccount `
-StorageAccountName $storageAccountName `
-ResourceGroupName $resourceGroupName
Sets the logs and metrics settings for the Key Vault #
To store the event log for Key Vault, you must use the Set-AzDiagnosticSetting cmdlet with the following syntax.
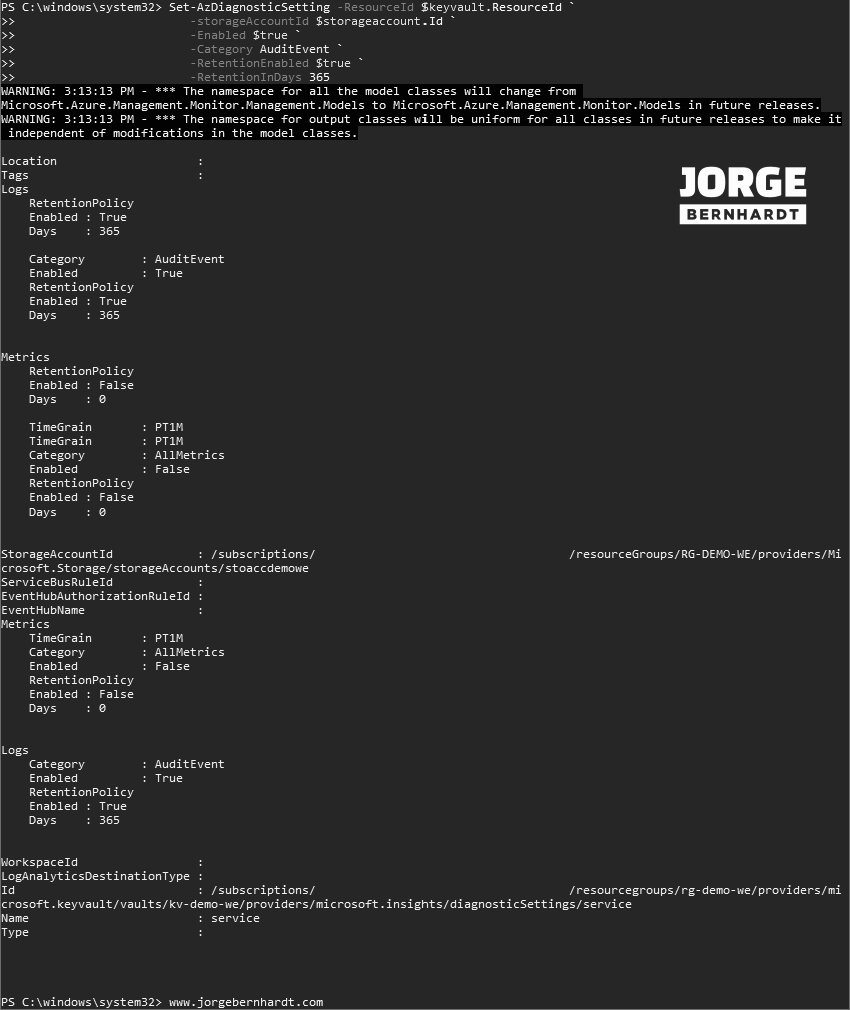
Set-AzDiagnosticSetting `
-ResourceId $keyvault.ResourceId `
-storageAccountId $storageaccount.Id `
-Enabled $true `
-Category AuditEvent `
-RetentionEnabled $true `
-RetentionInDays 365
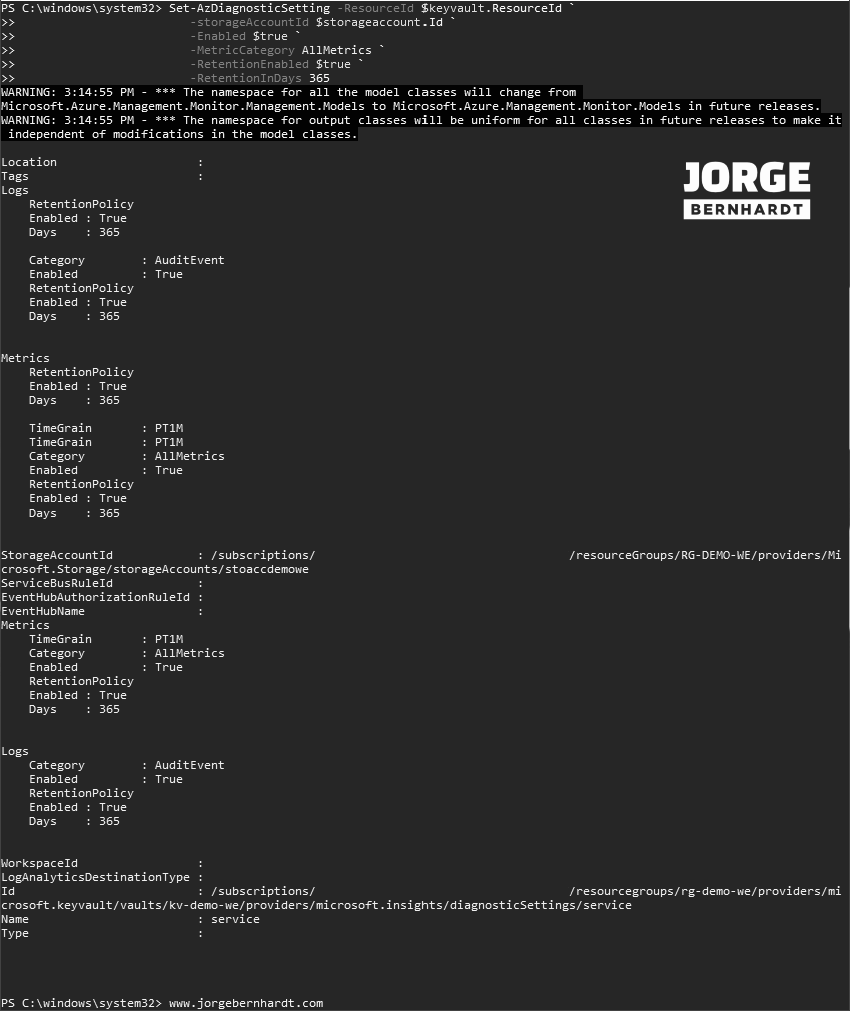
Set-AzDiagnosticSetting `
-ResourceId $keyvault.ResourceId `
-storageAccountId $storageaccount.Id `
-Enabled $true `
-MetricCategory AllMetrics `
-RetentionEnabled $true `
-RetentionInDays 365
Set-AzDiagnosticSetting `
-ResourceId $keyvault.ResourceId `
-storageAccountId $storageaccount.Id `
-Enabled $false
Azure CLI Workaround #
In this case, we will use Azure Cloud Shell, a browser-based shell built into Azure Portal. This allows us to use the Azure command-line tools (Azure CLI and Azure PowerShell) directly from a browser. If you want to know more about Azure Cloud Shell, check out this link. First, we define the characteristics of our environment and store the values in variables.
resourceGroupName="RG-DEMO-WE"
keyVaultName="KV-DEMO-WE"
storageAccountName="stoaccdemowe"
To improve the visualization of the following commands, I will store the resources into variables.
stoaccountid=$(az storage account show \
--name $storageAccountName \
--resource-group $resourceGroupName \
--query id --output tsv)
keyVaultid=$(az keyvault show \
--name $keyVaultName \
--query id \
--output tsv)
Sets the logs and metrics settings for the Key Vault #
To store the event log for Key Vault, you must use the following command.
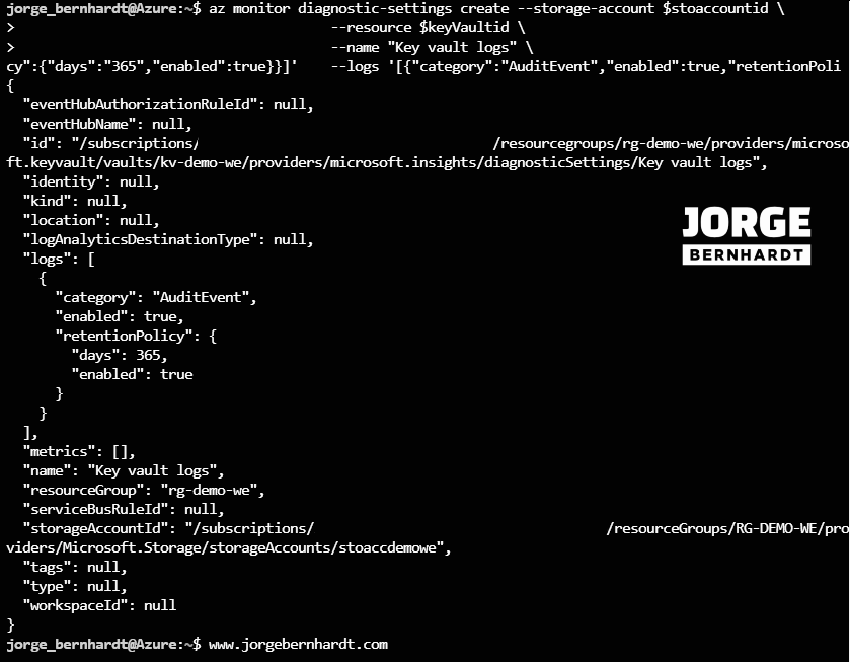
az monitor diagnostic-settings create \
--storage-account $stoaccountid \
--resource $keyVaultid \
--name "Key vault logs" \
--logs '[{"category":"AuditEvent","enabled":true,"retentionPolicy":{"days":"365","enabled":true}}]'
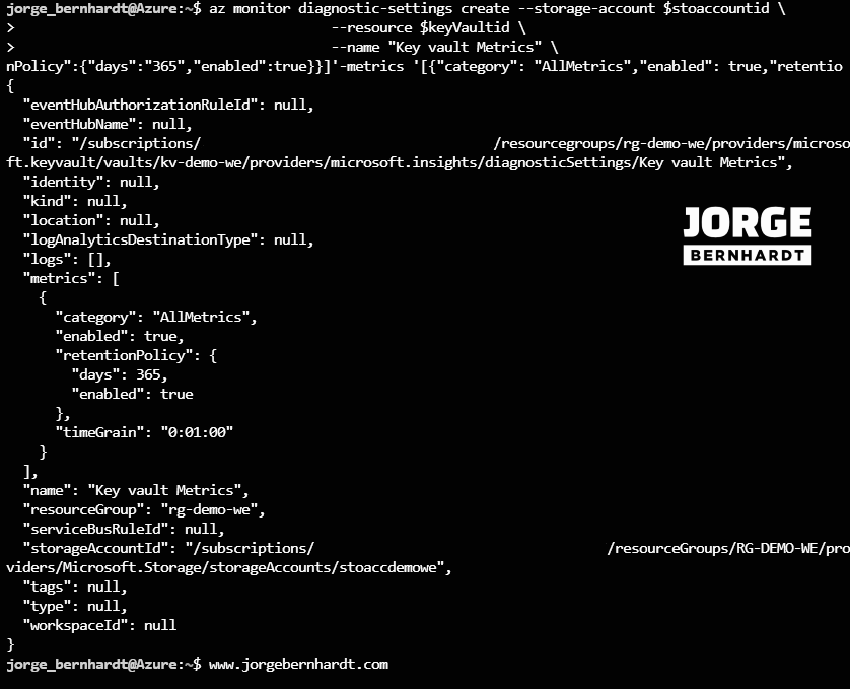
az monitor diagnostic-settings create \
--storage-account $stoaccountid \
--resource $keyVaultid \
--name "Key vault Metrics" \
--metrics '[{"category": "AllMetrics","enabled": true,"retentionPolicy":{"days":"365","enabled":true}}]'
az monitor diagnostic-settings create \
--storage-account $stoaccountid \
--resource keyVaultid \
--name "Key vault logs" \
--logs '[{"category": "AuditEvent","enabled": false}]'
az monitor diagnostic-settings create \
--storage-account $stoaccountid \
--resource keyVaultid \
--name "Key vault Metrics" \
--metrics '[{"category": "AllMetrics","enabled": false}]'
Thanks for reading my post. I hope you find it useful.
If you want to know more about Security recommendations for Azure Key vault, check out this link.
