Setting Private Endpoint for Azure Key Vault using Azure PowerShell
Hi everyone, and happy new year. In the first post of the year, I want to continue talking about Private Endpoints. In this post, I want to show you how to create a private endpoint to connect securely to an Azure Key Vault, and I’ll also show you how to use two features that Microsoft recently enabled support for Private Endpoint Static IP Configurations and support for customizing the name of the network interface assigned to the private Endpoint.
I will use a virtual machine (VM) on the same network for the test to check the private connection.
Some concepts that we must keep in mind before starting. #
- Azure Private Link
- Azure Private Link provides access to Azure services privately over the Microsoft Azure Backbone Network instead of publicly over the Internet.
- All incoming and outgoing traffic between your virtual network and the Azure service travels through the Microsoft Azure backbone.
- If you have Azure peered virtual networks, no additional configuration is required for those peered networks to access a private Azure resource.
- Azure Private Endpoint
- The private Endpoint is the read-only network interface that replaces the public Endpoint of the resource.
- The private Endpoint must be deployed in the same region and subscription as the virtual network.
- Private Endpoint is the base technology behind Private Link that enables a private connection between your Azure Virtual Network (VNet) and an Azure service.
- Private Endpoint is not a free service. You pay a flat rate per hour, as well as a flat rate per gigabyte for inbound and outbound traffic that passes through the private Endpoint.
- Azure Private DNS Zone
- A private DNS zone provides name resolution services within virtual networks.
- It can only be accessed from the virtual networks linked to it and is not accessible from the Internet.
- A private DNS zone can be linked to one or more virtual networks. Prerequisites
- This tutorial assumes that you already have an operational Azure key vault. You can use an existing one or if you want to create a new one, check out this link.
Azure PowerShell Workaround #
Check out this link if you want to know how to install the PowerShell Azure module on your machine.
The simplest way to get started is to sign in interactively at the command line.
Connect-AzAccount
This cmdlet will bring up a dialog box prompting you for your email address and password associated with your Azure account. You can choose the default subscription if you have more than one associated with your mail account. To perform this task, we will use the following commands:
Get-AzSubscription
Select-AzSubscription -Subscription "My Subscription"
Once you set your default subscription, you’re ready to start.
Here we define our environment’s characteristics and the resources’ names.
$resourceGroupName = "RG-DEMO-NE"
$location = "northeurope"
$vnetName = "VNET-DEMO-NE"
$keyVaultName = "KV-DEMO-NE"
I will store the resources into variables to improve the visualization of the following commands.
$keyVault = Get-AzKeyVault `
-Name $keyVaultName `
-ResourceGroupName $resourceGroupName
$virtualNetwork = Get-AzVirtualNetwork `
-ResourceName $vnetName `
-ResourceGroupName $resourceGroupName
$subnet = $virtualNetwork `
| Select-Object -ExpandProperty subnets `
| Where-Object Name -eq 'default'
Azure Private Link #
Azure Private Link enables you to access Azure PaaS Services over a private endpoint in your virtual network. First, you must create a private link service connection to Azure Key Vault before you create a private endpoint. The private link service connection is an input you will use to create the private Endpoint.
Determine GroupID #
Use the Get-AzPrivateLinkResource cmdlet to determine the GroupId of the resource. Depending on the resource type, one or more groupoids can be per resource.
(Get-AzPrivateLinkResource -PrivateLinkResourceId $keyVault.ResourceId).GroupId
Create the private link service connection #
Once you have the GroupID of the resource, you can create the private link service connection using the New-AzPrivateLinkServiceConnection cmdlet with the following syntax.
$privateLinkServiceConnection= New-AzPrivateLinkServiceConnection `
-Name 'keyvaultnelink' `
-PrivateLinkServiceId $keyVault.ResourceId `
-GroupId "vault"
Azure Private Endpoint #
A private endpoint is a network interface that uses a private IP address from your virtual network. This network interface connects you privately to a service that works with Azure Private Link.
Create a private endpoint for Azure Key Vault #
To set a static IP configuration for the private Endpoint, you should use the New-AzPrivateEndpointIpConfiguration cmdlet with the following syntax. But if you want to use a dynamic IP, you can omit this step and the parameter -IpConfiguration in the creation command.
$privateEndpointName = "keyvaultne"
$ipconfig = New-AzPrivateEndpointIpConfiguration `
-Name $privateEndpointName `
-PrivateIpAddress "10.2.0.98" `
-MemberName "default" `
-GroupId "vault"
Important: keep in mind that the assigned static IP must be free and belong to the range of IPs of the subnet in which you want to create the private Endpoint.
To create the private Endpoint, you should use the New-AzPrivateEndpoint cmdlet with the following syntax. This command creates a private endpoint with a specific private link service identifier on the specified subnet in a virtual network. If you want to customize the name assigned to the network interface, you should use the -CustomNetworkInterfaceName parameter.
New-AzPrivateEndpoint -Name $privateEndpointName `
-ResourceGroupName $resourceGroupName `
-Location $location `
-PrivateLinkServiceConnection $privateLinkServiceConnection `
-Subnet $subnet `
-IpConfiguration $ipconfig `
-CustomNetworkInterfaceName "NIC-VAULT-PRIVATELINK" `
-Tag @{Environment="www.jorgebernhardt.com"}
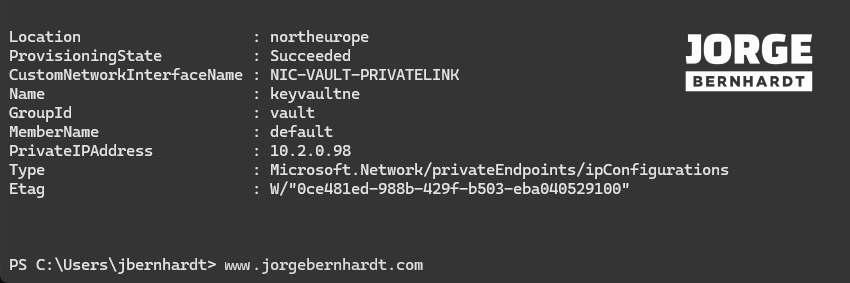
Once the private Endpoint has been created, you can check the properties as well as the state of the Endpoint using the Get-AzPrivateEndpoint cmdlet with the following syntax.
Get-AzPrivateEndpoint `
-Name $privateEndpointName `
-ResourceGroupName $resourceGroupName `
| Select-Object Location,ProvisioningState, CustomNetworkInterfaceName `
-ExpandProperty IpConfigurations
Azure Private DNS Zone #
Correctly configuring DNS settings is critical to resolving the private Endpoint’s IP address to the fully qualified domain name (FQDN) in the connection string. When you create a private endpoint, Azure changes the public name resolution by adding another CNAME record pointing towards the dedicated FQDN of the private Endpoint. The record name and zone depend on resource type (or sub-type), and you can find the reference of DNS zone naming from Microsoft’s documentation.
From my virtual machine located on the same network as the private Endpoint, I perform a check before creating the private DNS zone and get the following output.
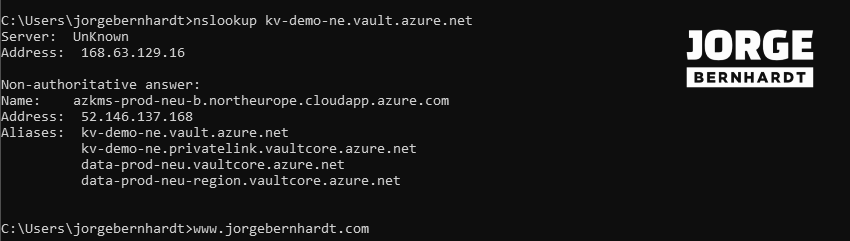
As you can see on the screenshot, the new record still points to the public IP, so you can still use the service publicly. But really, what we want is private access, so we need to create a private DNS zone with a record pointing to the private Endpoint’s IP; that’s the key point that really makes sense.
Create a Private DNS zone #
To create a private DNS zone, you should use the New-AzPrivateDnsZone cmdlet with the following syntax.
$privateZone = New-AzPrivateDnsZone `
-ResourceGroupName $resourceGroupName `
-Name "privatelink.vaultcore.azure.net" `
-Tag @{Environment="www.jorgebernhardt.com"}
Configure the Private DNS zone #
To create a private DNS zone group on the specified private Endpoint, you should use the New-AzPrivateDnsZoneGroup cmdlet with the following syntax.
$config = New-AzPrivateDnsZoneConfig `
-Name $privateZone.Name `
-PrivateDnsZoneId $zone.ResourceId
New-AzPrivateDnsZoneGroup `
-ResourceGroupName $resourceGroupName `
-Name "myZoneGroup" `
-PrivateEndpointName $privateEndpoint.Name `
-PrivateDnsZoneConfig $config
Add a virtual network link #
Last but not least, To have DNS resolution on the virtual network where the resources accessing the Azure Key Vault are located, you must link the private zone created in the previous step with the existing virtual network. To do this, you should use the New-AzPrivateDnsVirtualNetworkLink cmdlet with the following syntax.
New-AzPrivateDnsVirtualNetworkLink `
-ResourceGroupName $resourceGroupName `
-ZoneName $privateZone.Name `
-Name "dnslinkne" `
-VirtualNetworkId $virtualNetwork.Id `
-Tag @{Environment="www.jorgebernhardt.com"}
Important: Note that you don’t need to change the connection URL to the service. Therefore, any connection established to Azure Key Vault will work correctly.
Check connectivity to private Endpoint #
From my virtual machine located on the same network as the private Endpoint, once the private DNS zone is created and bound to the virtual network, I repeat the above check from my virtual machine and get the following output.
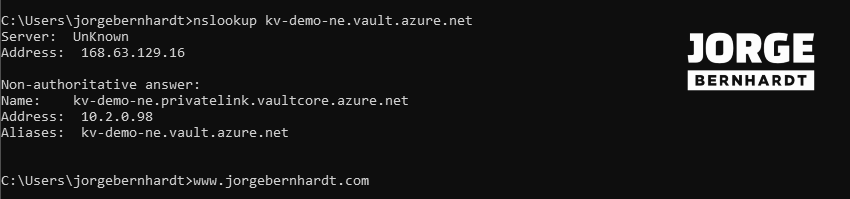
As you can see in the screenshot above, the Azure Key Vault endpoint now returns the assigned private IP.
Deny public network access #
Finally, you can use the following command to disable public access to the resource, but note that once this is done, only connections from private endpoints are allowed. All connections from public endpoints will be denied.
Update-AzKeyVault `
-VaultName $keyVaultName `
-ResourceGroupName $resourceGroupName `
-PublicNetworkAccess "Disabled"
You can check that the configuration has been set correctly with the following command.
(Get-AzKeyVault -VaultName $keyVaultName `
-ResourceGroupName $resourceGroupName).PublicNetworkAccess
Clean-up created resources #
If you want to delete the resources created during this article, running the following commands in the order listed is important to avoid dependency errors.
To remove a DNS zone group, you should use the Remove-AzPrivateDnsZoneGroup cmdlet.
Remove-AzPrivateDnsZoneGroup `
-Name "myZoneGroup" `
-ResourceGroupName $resourceGroupName `
-PrivateEndpointName $privateEndpointName `
-Force
To remove a virtual network link from the private DNS zone, you should use the Remove-AzPrivateDnsVirtualNetworkLink cmdlet.
Remove-AzPrivateDnsVirtualNetworkLink `
-Name "dnslinkne" `
-ResourceGroupName $resourceGroupName `
-ZoneName "privatelink.vaultcore.azure.net"
Once the previous two commands have been executed successfully, you can delete the private DNS zone using the Remove-AzPrivateDnsZone cmdlet.
Remove-AzPrivateDnsZone `
-ResourceGroupName $resourceGroupName `
-Name "privatelink.vaultcore.azure.net"
Using the Remove-AzPrivateEndpoint cmdlet, you can delete the created Private Endpoint.
Remove-AzPrivateEndpoint `
-ResourceGroupName $resourceGroupName `
-Name $privateEndpointName `
-Force
Finally, you can run the following command to enable public access to the Azure Key Vault again.
Update-AzKeyVault `
-VaultName $keyVaultName `
-ResourceGroupName $resourceGroupName `
-PublicNetworkAccess "Enabled"
You can check that the configuration has been set correctly with the following command.
(Get-AzKeyVault -VaultName $keyVaultName `
-ResourceGroupName $resourceGroupName).PublicNetworkAccess
Thanks for reading my post. I hope you find it helpful.
Check out this link for more information about Azure private endpoints.
