How to update the tenant ID in an Azure key vault
I recently migrated an Azure subscription to a new tenant, and in the key vault resources, I had to perform a few additional steps that I want to show you. So In this week’s article, we’ll look at updating the tenant ID and removing previous access policies and role assignments to the key vault resource once it’s moved to the new subscription.
Prerequisites
- You must have Contributor level access or higher on both the current subscription where your Key vault exists and the subscription to which you want to move your key vault.
Azure PowerShell Workaround #
Check out this link if you want to know how to install the PowerShell Azure module on your machine.
The simplest way to get started is to sign in interactively at the command line.
Connect-AzAccount
This cmdlet will bring up a dialog box prompting you for your email address and password associated with your Azure account. If you have more than one subscription associated with your mail account, you can choose the default subscription. To perform this task, we will use the following commands:
Get-AzSubscription
Select-AzSubscription -Subscription "My Subscription"
Once you set your default subscription, you’re ready to start.
Set the variables #
Here we define the environment’s characteristics and the resources’ names.
$keyvaultName="KV-DEMO"
Check current settings #
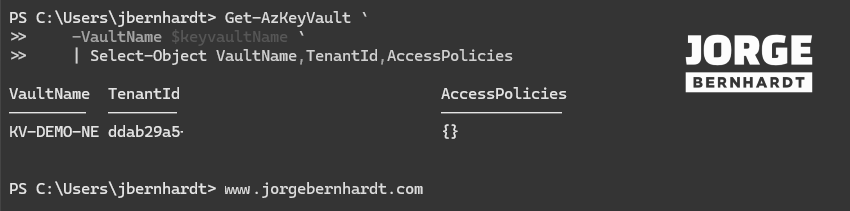
First, we check the current configuration using the Get-AzKeyVault cmdlet with the following syntax.
Get-AzKeyVault `
-VaultName $keyvaultName `
| Select-Object VaultName,TenantId,AccessPolicies
Get the properties for the key vault #
To improve the visualization of the code, I’ll store the key vault resource in an object. For this, I use the following command.
$vault = Get-AzResource `
-Name $keyvaultName `
-ExpandProperties
Remove old access policies #
You can set an empty array to remove the access policy setting from the key vault object.
$vault.Properties.AccessPolicies = @()
Set new tenant id #
You can use the following command to assign the new tenant ID value to the key value object.
$vault.Properties.TenantId = (Get-AzContext).Tenant.TenantId
Update the key vault’s properties #
With the properties set on the key vault object, we’ll use the following command to update the properties of the key vault resource.
Set-AzResource `
-ResourceId $vault.Id `
-Properties $vault.Properties `
-Force
Check the changes made #
As always, at the end of an update or modification of an Azure resource, we verify that the current configuration of the resource is as expected. For this, we will use the following command.
Get-AzKeyVault `
-VaultName $keyvaultName `
| Select-Object VaultName,TenantId,AccessPolicies
Remove key vault role assignments #
Once your vault is associated with the correct tenant ID, delete old access policy entries or role assignments and set new access policy entries or role assignments.
Use the following command to get a list of role assignments on your key vault resource.
Get-AzRoleAssignment `
-Scope $vault.Id `
| Select-Object ObjectId,ObjectType,RoleDefinitionName,Scope
Identify and remove outdated role assignments. Replace the values in the example command with your values.
Remove-AzRoleAssignment -ObjectId 751007cf-be4e-4e06-8983-b438e2cd012b `
-RoleDefinitionName "Reader" `
-Scope '/subscriptions/0000-0000-0000-0000-0000/resourceGroups/RG-DEMO/providers/Microsoft.KeyVault/vaults/KV-DEMO'
Azure CLI Workaround #
In this case, we will use Azure Cloud Shell, a browser-based shell built into Azure Portal. This allows us to use the Azure command-line tools (Azure CLI and Azure PowerShell) directly from a browser. If you want to know more about Azure Cloud Shell, check out this link.
Here we define our environment’s characteristics and the resources’ names.
keyvaultName="KV-DEMO"
tenantId=$(az account show --query tenantId)
Check current settings #
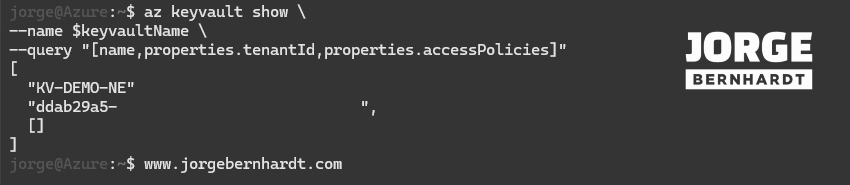
First, check that the current configuration of the Key vault does not have the expected tenant id using the following command.
az keyvault show \
--name $keyvaultName \
--query "[name,properties.tenantId,properties.accessPolicies]"
Update the key vault’s properties #
To update the key vault resource properties, use the following command
az keyvault update \
--name $keyvaultName \
--set Properties.tenantId=$tenantId \
--remove Properties.accessPolicies
Check the changes made #
To verify that the current configuration of the resource is as expected, use the following command.
az keyvault show \
--name $keyvaultName \
--query "[name,properties.tenantId,properties.accessPolicies]"
Remove key vault role assignments #
Once your vault is associated with the correct tenant ID, delete old access policy entries or role assignments and set new access policy entries or role assignments.
Use the following command to get a list of role assignments on your key vault resource.
az role assignment list \
--scope $keyvaultid \
--include-inherited \
--query "[].{Id:principalId,Type:principalType,Role:roleDefinitionName,Scope:scope}"
Identify and remove outdated role assignments. Replace the values in the example command with your values.
az role assignment delete \
--assignee "c0672d5d-3443-4fd3-a359-fc353ad3bf79" \
--role "Contributor" \
--scope "/subscriptions/000-000-000-000-000/resourceGroups/RG-DEMO/providers/Microsoft.KeyVault/vaults/KV-DEMO"
Thanks for reading my post. I hope you find it helpful.
Check out this link for more information on transferring an Azure subscription to a different Azure AD directory.
