How to create a Group Managed Service Accounts (gMSA)
In this post, I want to show you how to create and use Group managed service accounts (gMSA). Before starting, I would like to identify the basic concepts and requirements.
Basic concepts #
- They can be used only on Servers running Windows Server 2012 or later.
- You can use the same Managed service account across multiple servers.
- Managed group service accounts are stored in the managed service account container of the active directory.
Requirements #
- Microsoft Active Directory must be present.
- Extend your Active Directory schema to Windows Server 2008 R2.
- Microsoft .Net framework 3.5 or above.
- PowerShell Active Directory module.
- At least one domain controller in the domain must be running Windows Server 2012.
- Microsoft Key Distribution Service up and running.
- Only members of Domain Admins or Account Operators groups can create a group managed service account objects.
All cleared. Now we can start.
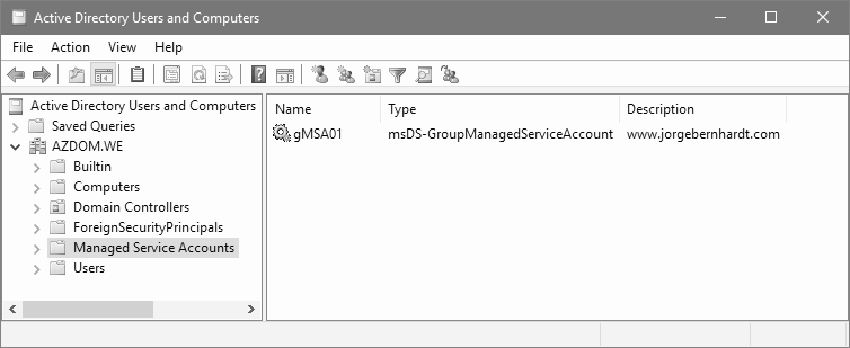
Create the Managed Service Account in Active Directory #
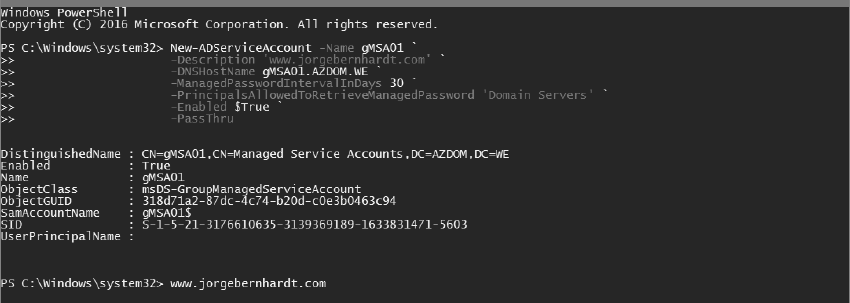
To create a gMSA with PowerShell, use the New-ADServiceAccount cmdlet with the following syntax:
New-ADServiceAccount `
-Name <String> `
-Description <String> `
-DNSHostName <String> `
-ManagedPasswordIntervalInDays <Int32> `
-PrincipalsAllowedToRetrieveManagedPassword <ADPrincipal[]> `
-Enabled $True | $False `
-PassThru
Run the following PowerShell command as administrator. The correct execution of the command returns the active directory object.
Parameters #
- -DNSHostName Defines the DNS hostname of service.
- -ManagedPasswordIntervalInDays Specifies the number of days for the password change interval.
- -PrincipalsAllowedToRetrieveManagedPassword Specifies the group of servers that can use a group managed service account. If the group defined in this parameter has been created by you, it is important to restart the host before installing the gMSA.
Install the gMSA on the host #
The Install-ADServiceAccount cmdlet installs an existing gMSA on the server on which the cmdlet is run. Use the cmdlet with the following syntax:
Install-ADServiceAccount `
-Identity <ADServiceAccount>
Run the following PowerShell commands as administrator.

Test-AdServiceAccount `
-Identity <ADServiceAccount>
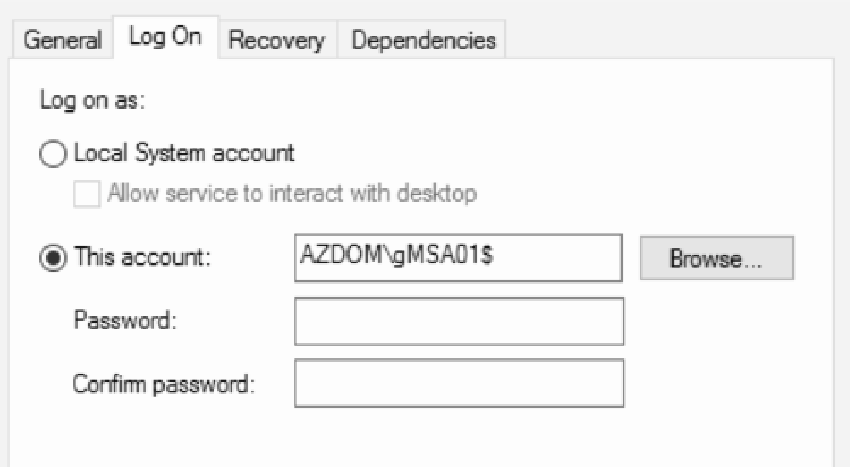
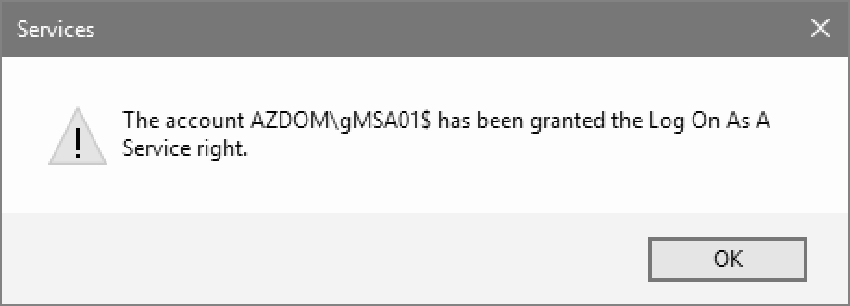
You can now use the gMSA for a service, a group of IIS applications, or a scheduled task. To do this, you must use the name of the account with $ at the end and leave the password blank.
If you want to know more about Group managed service accounts, check out this link.
